A glance at our cybersecurity risk assessment
At AbriteLogic Solutions, our trusted vCISO experts have assembled top-tier professionals to help client organizations through the cybersecurity risk assessment process to improve their cyber resilience and compliance programs to reduce risks.
- Our team of experts understands that there’s no one-size-fits-all solution for risk assessment.
- We also know that every organization faces its unique sets of cyberthreats and security risks, so our team can tailor the risk assessment process to your needs.
“All courses of action are risky, so prudence is not in avoiding danger (it’s impossible), but calculating risk and acting decisively.”
~Niccolo Machiavelli~
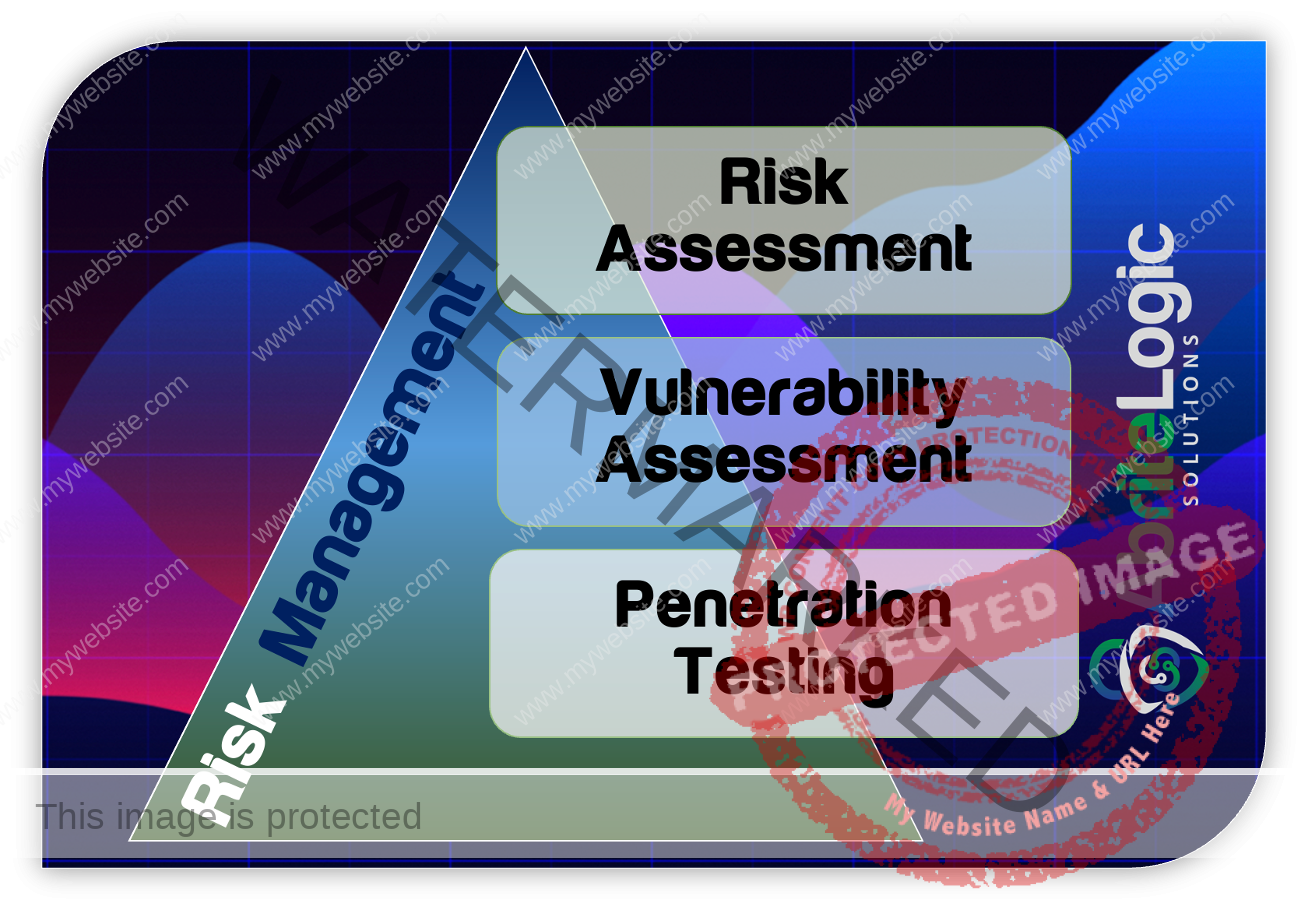
Key Considerations For Effective Risk Assessment
To perform a cybersecurity risk assessment, it’s essential to assemble a team with the right qualifications and mindset to be compliant with the relevant industry frameworks. Armed with new technical expertise and insights, we provide remediation actions and prioritize preemptive measures to address risks and harden your security. Therefore, our trusted team of experts will help drive your risk management strategy to mitigate the risks to your critical systems and data.
NIST Frameworks
- Required guidelines and procedures to establish and maintain security controls
- Trusted advice for choosing the right IT security framework for your organization
- NIST 800-53, NIST 800-37, NIST 800-137
- NIST Cybersecurity Framework (CSF)
- Other frameworks as applicable and depending on your specific needs
SOC1/SOC2/SOC3 Compliance
- Utilizing Type I and Type II reports to check suitability and operating effectiveness of the controls
- SOC 1: Type 1 & 2
- SOC 2: Type 1 & 2
- SOC 3 Reports
HIPAA Compliance
- Assisting healthcare providers, health insurance companies, and health maintenance organizations to remain compliant with the HIPAA law
- Helping define the security and privacy for PHI and ePHI and build your security program using controls mapped to HIPAA
PCI/DSS Compliance
- Working with organizations providing, storing, or using payment card data to get PCI/DSS certified by meeting all stated requirements
- Expertise in varying PCI compliance Levels 1, 2, 3, & 4 depending on whether it involves a merchant or service provider
FedRAMP Compliance
- Providing expertise for the FedRAMP authorization process via documenting, assessing, authorizing, and monitoring
- Enjoying the benefits of understanding the requirements for FedRAMP certification
FISMA Compliance
- Ensuring FISMA compliance best practices including information system inventory, risk categorization, system security plan and controls
- Utilizing FIPS 199 standards for security categorization and FIPS 200 standards for minimum security requirements

The Benefits Of Our Risk Assessments
Taking a risk-based approach to cybersecurity starts with understanding and aligning business objectives to cybersecurity goals where risk management plays a key role.
Selected list of client-focused services:
- The AbriteLogic Solutions team is charged with helping you catalog and categorize information assets, assess and analyze the risk, and select and implement appropriate security controls.
- Bringing knowledgeable and experienced vCISO experts at your disposal with proven processes and toolsets that enable your business to implement appropriate security controls to mitigate risks.
- Understanding your unique situations and providing guidance on setting clear expectations for safeguarding your critical systems and assets.
Why Chose Our vCISO Services?
The following is the scope of our key vCISO responsibilities related to service offering and why you should count on us:
- Helping client organizations identify potential threats and vulnerabilities, and mitigating them to prevent or minimize potential security incidents and cyberattacks, which is required to facilitate your business operations in the long term.
- Providing expert advice and assessment on strategic security planning, security threats, and compliance requirements.
- Providing consultation to develop an effective cybersecurity program and facilitate its integration into your business strategy, process, and culture.
- Holding ourselves to the highest ethical standards and treating all clients with dignity and respect.
- Remaining passionate about fast and quality deliverables throughout our service delivery cycle and ensuring that project deliverables conform to quality standards while exceeding expectations.
- Claiming ownership for the results of our actions and expertise; therefore, we understand that maintaining consistent and effective communication is the key to a successful engagement.

