Incident Response Planning (IRP)
Related Services
Overview of Our Incident Response Services
Certainly, while the costs associated with a single data breach are certainly high in terms of financial loss, reputational damage, and legal liability, the real impact on businesses is the loss of consumer trust and revenue. Without customers, there is no revenue and hence no business.
Cyberattacks and data breaches continue to evolve and increase both in frequency and severity; therefore, creating and testing incident response playbooks to increase cyber resilience remains imperative.
Our trusted team of cybersecurity professionals has an incident-driven IR solution that can help you build trust with your customers. In other words, we can guide and create a proactive and coordinated incident response plan, which outlines your organization’s response to security incidents such as data breaches, data leaks, and cyberattacks.

“Tardiness often robs us opportunity, and the dispatch of our forces.”
~Niccolo Machiavelli~
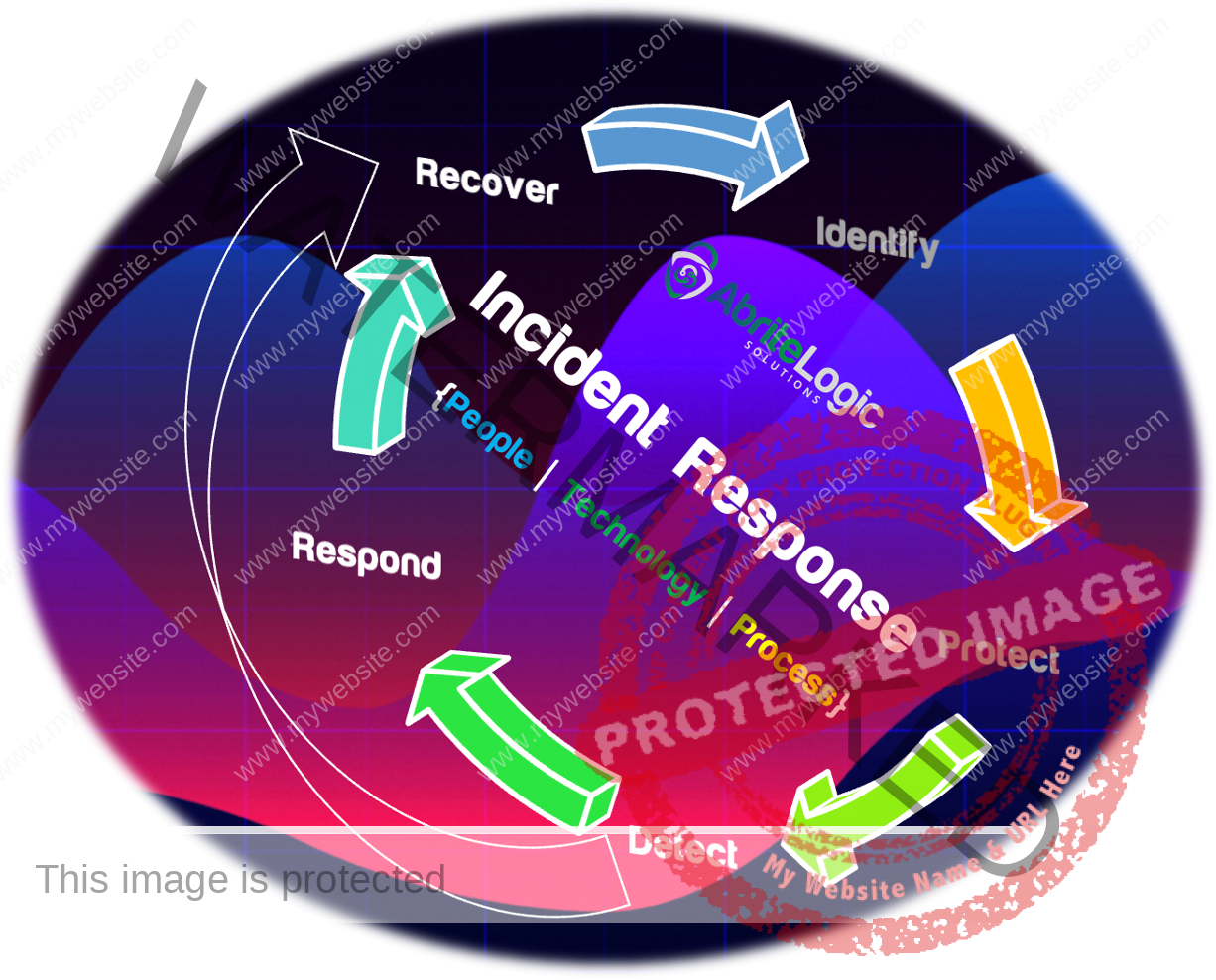
Key Considerations For Incident Response Plan (IR)
Then AbriteLogic Solutions will guide and help you accomplish your security objectives with the following considerations for IR planning and development. The key to the best protection revolves around a culture of instituting a thorough and robust incident response plan.
NIST-Based IR Phases
- Preparation and Triag
- Detection and Analysis
- Containment and Eradication
- Post-incident Recovery
- Lessons Learned
IR Methodology
- Scope Definition
- Communications
- Evidence Preservation
- Operational-Level Engagements
- Training and Awareness
IR Team (CSIRT)
- IR Manager
- Security Analysts
- Threat Researchers
- IR Coordinator
- Executive Response Team
Immediate Benefits
- Data Protection
- Enhanced Reputation
- Cost Reduction
- Resiliency
- Competitive Advantage

The Benefits Of Our IR Engagements
Whether you have Computer Security Incident Response Team (CSIRT) or not, our team will work with your team to develop a versatile IR plan as a result of collecting, analyzing, and acting upon data from a security incident. We are committed to helping our clients build and grow a security-aware culture that fosters a high-security posture within your organization.
Our client-focused approaches
- Conducting an incident-driven IR plan used with best practices to mitigate cyberattacks and data breaches.
- Armed with IR expertise, bring knowledgeable and experienced vCISO experts with proven processes and toolsets that enable your business to maintain appropriate security culture and resilience.
- Understanding your unique situations and providing guidance on setting clear expectations for safeguarding your critical systems and assets while meeting regulatory compliance.
Why Chose Our vCISO Services?
The following is the scope of our key vCISO responsibilities related to service offering and why you should count on us:
- Helping client organizations maintain a robust IR plan to mitigate ever-evolving security breaches. Whether you have Computer Security Incident Response Team (CSIRT) or not, our team will work with your team to collect, analyze, and act upon data from a security incident.
- Providing expert advice and assessment on strategic security planning, security threats, and compliance requirements.
- Providing consultation to develop an effective cybersecurity program and facilitate its integration into your business strategy, process, and culture.
- Holding ourselves to the highest ethical standards and treating all clients with dignity and respect.
- Remaining passionate about fast and quality deliverables throughout our service delivery cycle and ensuring that project deliverables conform to quality standards while exceeding expectations.
- Claiming ownership for the results of our actions and expertise; therefore, we understand that maintaining consistent and effective communication is the key to a successful engagement.

